| Security of data in transit over the Internet
becomes increasingly necessary because of steadily growing data
volume and importance. Nowadays, every user of a public network
sends various types of data, from email to credit card details
daily, and he would therefore like them to be protected when in
transit over a public network. To this end, a practical SSL protocol
has been adopted for protection of data in transit that encompasses
all network services that use TCP/IP to support typical application
tasks of communication between servers and clients. |

The SSL protocol was originally developed by Netscape, to ensure security
of data transported and routed through HTTP, LDAP or POP3 application
layers. SSL is designed to make use of TCP as a communication layer to
provide a reliable end-to-end secure and authenticated connection between
two points over a network (for example between the service client and the
server). Notwithstanding this SSL can be used for protection of data in
transit in situations related to any network service, it is used mostly in
HTTP server and client applications. Today, almost each available HTTP
server can support an SSL session, whilst IE or Netscape Navigator browsers
are provided with SSL-enabled client software.
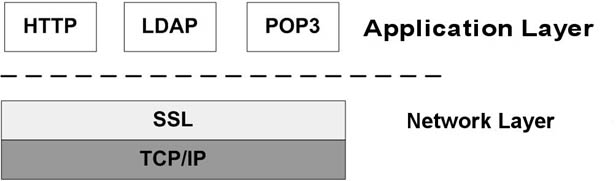
Figure 1 SSL between application protocols and TCP/IP
SSL objectives and architecture
Which problems does SSL target? The main objectives for SSL are:
- Authenticating the client and server to each other: the SSL protocol
supports the use of standard key cryptographic techniques (public key
encryption) to authenticate the communicating parties to each other.
Though the most frequent application consists in authenticating the
service client on the basis of a certificate, SSL may also use the same
methods to authenticate the client.
- Ensuring data integrity: during a session, data cannot be either
intentionally or unintentionally tampered with.
- Securing data privacy: data in transport between the client and the
server must be protected from interception and be readable only by the
intended recipient. This prerequisite is necessary for both the data
associated with the protocol itself (securing traffic during
negotiations) and the application data that is sent during the session
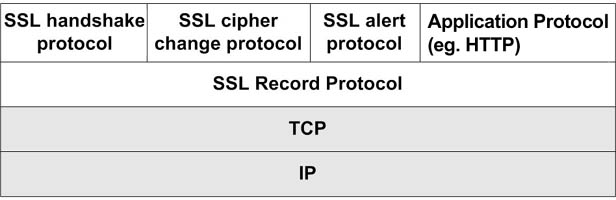
itself. SSL is in fact not a single protocol but rather a set of
protocols that can additionally be further divided in two layers:
- the protocol to ensure data security and integrity: this layer is
composed of the SSL Record Protocol,
- the protocols that are designed to establish an SSL connection:
three protocols are used in this layer: the SSL Handshake Protocol, the
SSL ChangeCipher SpecPprotocol and the SSL Alert Protocol.
The SSL protocol stack is illustrated in Figure 2.